A Web Application Firewall (WAF) is a security tool designed to protect web applications by filtering and monitoring HTTP traffic between a web application and the Internet. It sits between the web application and the client and analyzes incoming traffic, looking for suspicious activity that may indicate an attack. The WAF then blocks or filters any malicious traffic or requests, preventing attackers from accessing or exploiting vulnerabilities in the web application.
WAFs are designed to protect web applications from a wide range of attacks, including SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), file inclusion, and other common web application vulnerabilities. They typically use a combination of signature-based and behavior-based detection methods to identify and block attacks.
WAFs can be implemented as software or hardware solutions and are typically configured to work in conjunction with other security measures, such as intrusion detection and prevention systems (IDS/IPS), to provide a comprehensive defense against web-based attacks.
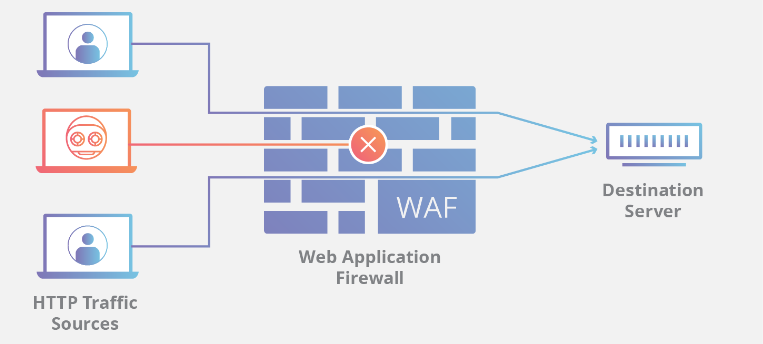
In ASP.NET, the Web Application Firewall (WAF) is implemented as a middleware component that sits between the client and the web server. The WAF intercepts all requests and responses and analyzes them for potential security threats, such as SQL injection attacks, cross-site scripting (XSS) attacks, and cross-site request forgery (CSRF) attacks.
ASP.NET provides a WAF implementation as part of Microsoft.AspNetCore.Mvc.Core package. This middleware component can be configured to apply a set of security rules to incoming requests, and it can also block requests that violate these rules.
To use the ASP.NET WAF, you first need to add Microsoft.AspNetCore.Mvc.Core package to your project. Then, you can configure the middleware component by adding it to the request processing pipeline in your Startup.cs file. Here's an example:
using Microsoft.AspNetCore.Builder;
using Microsoft.AspNetCore.Hosting;
using Microsoft.AspNetCore.Mvc;
using Microsoft.Extensions.Configuration;
using Microsoft.Extensions.DependencyInjection;
using Microsoft.Extensions.Hosting;
namespace MyWebApplication
{
public class Startup
{
public Startup(IConfiguration configuration)
{
Configuration = configuration;
}
public IConfiguration Configuration { get; }
public void ConfigureServices(IServiceCollection services)
{
services.AddMvc();
}
public void Configure(IApplicationBuilder app, IWebHostEnvironment env)
{
// Add the WAF middleware to the request pipeline
app.UseMvcWithDefaultRoute();
app.UseMiddleware<Microsoft.AspNetCore.Mvc.Core.MvcMiddleware>();
}
}
}
Once the middleware component is added to the pipeline, you can configure it by specifying a set of security rules in your appsettings.json file. Here's an example:
{
"WafOptions": {
"AllowedHosts": [ "example.com", "*.example.com" ],
"BlockedUris": [ "/admin/*", "*.php", "*.asp" ],
"BlockOnViolation": true
}
}
In this example, the AllowedHosts property specifies a list of allowed host names, the BlockedUris property specifies a list of blocked URIs, and the BlockOnViolation property indicates whether requests should be blocked when a security rule is violated.
ASP.NET also provides additional WAF options that allow you to customize the security rules and configure logging and monitoring. You can find more information on the ASP.NET WAF in the official Microsoft documentation.